Your scenario with automations from JSM and Jira Software
You have set up an automation that imports all Jira Service Management tickets one-to-one into Jira Software. For example, as soon as a customer creates a ticket of the type “error message”, the automation kicks in and a linked Jira issue is created for your development department.
The problem with request participants and security level schemes
If request participants and security level schemes are involved in this process, the synchronization to Jira software unfortunately does not work properly. The created tasks are mirrored, but the request participants from Jira Service Management are not transferred to Jira. This means that they cannot see and edit the linked tickets in Jira – a big problem. It is caused by the security level schemes in Jira, as there is no “request participant” field selectable in them. Simply disabling the security levels would not be a solution, as you would rather not compromise data privacy regulations. Atlassian is aware of the difficulty, but has not yet been able to provide a straightforward solution. But no worries, Actonic is here for you and jumps in with the most efficient workaround and solution for this issue?
How to automatically add request participants
The first, simplest and most obvious idea is an automation like: If case is created, then edit case as follows … But this doesn’t work because there is no option to add the field “Request participant” for processing.
You can’t add observers as a field, either.
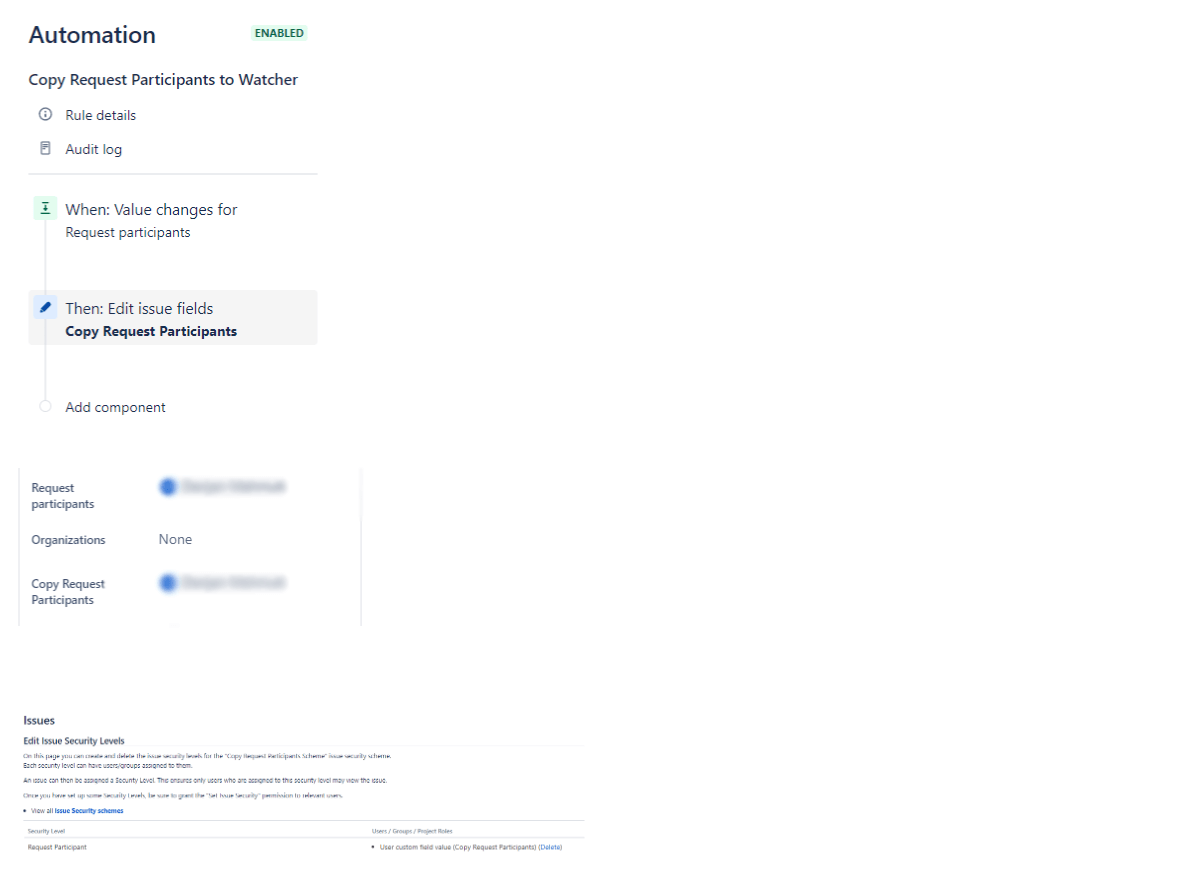
What you can do is to create an automation with these rules:
-
Trigger: When the “Request Participant” field in JSM changes (when something is added or deleted)
-
Then: Copy the changed value into the custom field “Copy Request Participants”:
This way you can keep both your request participants and your security level schemes.
Summary for your success with request participants in Jira
So, to automatically transfer your Jira Service Desk/Management request participants to Jira Software and keep the security levels, you have to create a custom field in Jira that performs the function of request participants. For, you can easily select custom fields in Jira security schema.
To get your problem solved, two automations are up and about.
-
Mirror the tickets from Jira Service Management to Jira Software
-
Copy the values of the request participants
If you follow our instructions, you can quickly and easily solve your synchronization problem. We will be happy to support you with your project. Just contact us!


 Gain hands-on insights from live webinars
Gain hands-on insights from live webinars