We, instead, want to work with you to analyze the healthcare data breaches of 2022 and find solutions for how you can avoid ending up on the Wall of Shame as well.
HIPAA violations in 2022
In 2022, 600 healthcare data breaches were reported by the HHS Office of Civil Rights. Among the most common HIPAA breaches were:
A breach of the Health Insurance Portability and Accountability Act (HIPAA) is more than expensive. Often, there is also the added concern of patient safety. After all, cyberattacks typically cause IT systems to fail. It’s unthinkable to run a medical practice or clinic if diagnostic and treatment data are unavailable.
Therefore, the following list is intended to guide us in making the critical healthcare systems more secure.
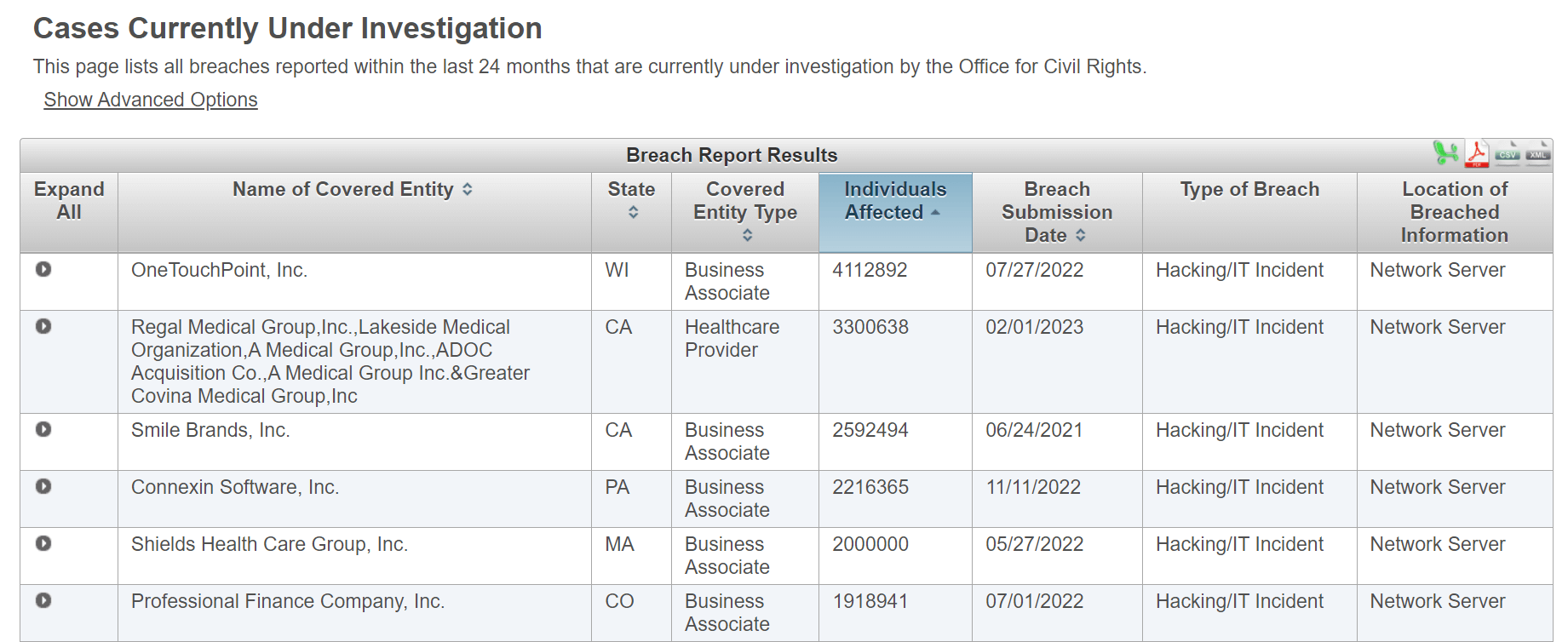
OneTouchPoint: 4.1 million affected patients
OneTouchPoint is a Wisconsin-based company that provides mailing, marketing and other services to healthcare organizations. In April 2022, unauthorized file access occurred to certain servers. Sensitive protected health information (PHI) such as names, patient records, ID numbers, patient demographics or service descriptions were exposed.
Many of the 35 healthcare organizations that use OneTouchPoint blame the company for reporting the security breach too late.
Lessons learned from this breach
-
Review your security measures regularly
-
Make sure your programs are HIPAA-compliant
-
Report HIPAA violations in a timely manner (within 60 days)
Advocate Aurora Health: 3 million affected patients
Advocate Aurora Health is one of Chicago’s largest healthcare providers, which runs 27 hospitals. In this HIPAA breach, certain internet tracking technologies from Google and Facebook led to the leak of some protected health information (PHI). These snippets of code, called pixels, were used to track interactions on patient portals. To prevent further harm, they have now been removed or disabled.
Lessons learned from this breach
Shields Healthcare Group: 2 million affected patients
Shields Healtcare Group was the victim of a cyberattack from March 7 to March 21, 2022. This company is a third-party vendor that provides MRI and ambulatory surgical services. The sensitive health data of more than 2 million patients was compromised during this period. However, the HIPAA violation was not discovered until March 28. Patient IDs, treatment information, insurance details and other data were stolen.
Lessons learned from this breach
Broward Health: 1.35 million patients affected
In January 2022, Broward Health suffered data theft of 1.34 million patients and employees through the hack of a connected third-party vendor. In this case, affected individuals were also notified after the 60-day deadline. Social Security numbers, insurance information, account numbers and medical information were exposed. The cause of the HIPAA violation was believed to be a lack of multi-factor authentication, which allowed an unauthorized party to gain access to the Broward Health network through a third-party vendor’s office.
Lessons learned from this breach